Phishing & Brand Abuse
One of the biggest security concerns from our customers is web-based phishing campaigns and brand abuse.
We have seen the implementation of DV and EV certificates that try to provide an enchanced level of trust - but this simply does not work. In response certificate costs have risen against well known brands, these heavy costs may prevent or dissuade attackers to create fake domains and attempt to legitamise them through signing freely available SSL certificates. A cheaper alternative is usually to attack the brand through subdomains, available cheaper top-level-domains (eg. *.dk, *.vip, *.online), or typo-squatted domains.
Instead of going after gmail.com, its easier for attackers to pick a name or keyword or number of keywords and register those domains and request SSL certificates. E.g.
- gmail.example.com
- mybank.secure.example.com
- secure-mybanking.example.com
Can we really Trust CA's
Sites obtain digital certificates from trusted third parties called Certificate Authorities (CAs). CAs validate the operator’s ownership of a domain before issuing them a certificate. If the issuing CA for a certificate is trusted by the browser, then that certificate can be used to serve content over HTTPS to visitors of the site. All this happens under the hood of the browser and is only surfaced to user by the little green lock in your address bar, or a nasty error message if things go wrong.
The Web’s PKI is an elaborate and complicated system. There are dozens of organizations that operate the certificate authorities trusted by popular browsers. Different browsers manage their own “root programs” in which they choose which certificate authorities are trusted. Becoming a trusted CA often requires passing an audit (WebTrust for CAs) and promising to follow a set of rules called the Baseline Requirements. These rules are set by a standards body called the CA/Browser forum, which consists of browsers and CAs. Each root program has their own application process and program-specific guidelines.
This system works great, until it doesn’t. As a system of trust, there are many ways for the PKI to fail. One of the risks inherent in the web PKI is that any certificate authority can issue any certificate for any website. That means that any CA can issue a certificate valid for gmail.com or facebook.com, and every browser will trust it. This forces users to put a lot of faith in certificate authorities and hope they don’t misbehave by issuing a certificate to the wrong person. Even worse, if a CA gets hacked, then an attacker could issue any certificate without the CA knowing, putting users at an even greater risk.
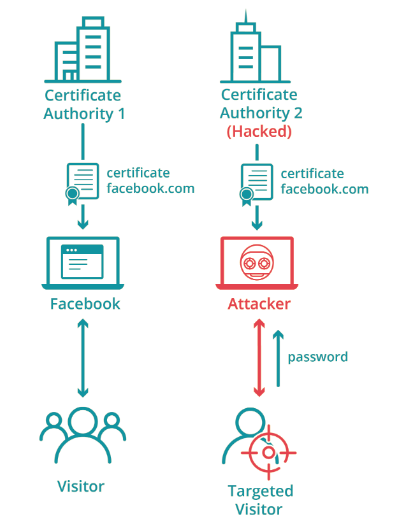
Why we use CT Logs
If all certificates are public, then so are mis-issued certificates. Certificate Transparency brings accountability to the web PKI using a technology. It puts trusted certificates into a list and makes that list available to anyone. That sounds easy, but given the decentralised nature of the internet, there are many challenges in making this a reliable bedrock for accountability.
A monitor is a service that helps alert websites of mis-issuance. It crawls logs for new certificates and alerts website owners if a new certificate is found for their domain. Popular monitors include SSLMate’s CertSpotter and Facebook’s Certificate Transparency Monitoring.
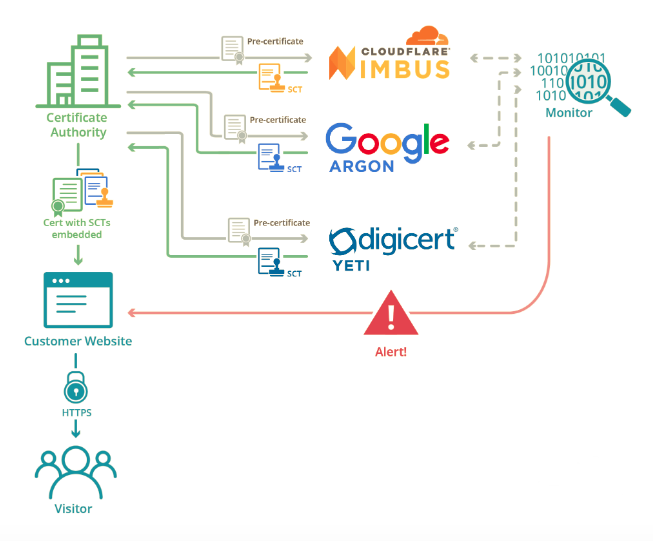
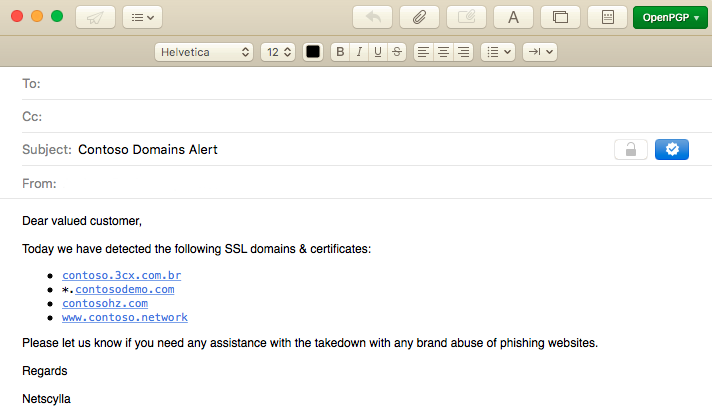
Why Netscylla
Instead of limiting you to searching domains (e.g. example.com), we permit you to search via a keyword or organisation name (e.g. example, mybank, myorgname). We believe this gives you more coverage and awareness in the certificate transparency logging world; Enhances the capabilities of your blue/SOC/monitoring teams, whereby they can quickly detect new phishing websites or brand abuses, as soon as possible; Or in the case of phishing, orchestrate the takedown of the domain before the campaign has been launched at your company.
Contact
Should you wish to enquire more about our offering, or request a demo. Please contact us.